Notice of Recent Security Incident
To All Workamper News Members,
I am writing to inform you that yesterday afternoon we experienced an unfortunate cybersecurity event within our bulk emailing system. An unauthorized user gained access to the email system and used it to send an email with a malicious link to all of our contacts.
We utilize a third-party system for sending bulk emails to our members that is completely separate from Workamper.com. As such, sensitive member data on Workamper.com is not as accessible in or by that email system. The customer data stored in the email system would only be your name and contact information. There is no credit card information, no password, no resume data, no ad data, and no order data stored there.
The email system that the nefarious character gained access to does not allow exporting of user data so all they were able to do was send an email out to our contacts.
If you received an email with the subject line "Transaction Alert" asking you to view a payment confirmation file by clicking a weird looking link, please just delete it.
This is what the malicious email looked like:
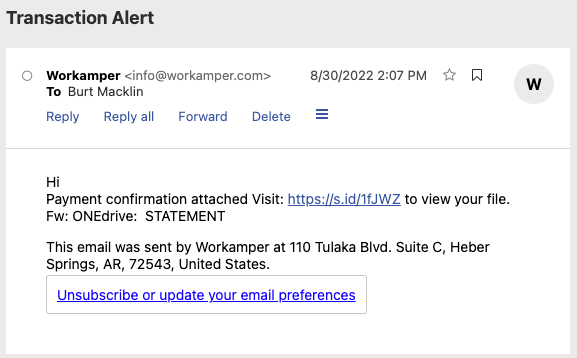
Based on the website link the unauthorized user included in the email, they are attempting to obtain peoples' personal email address account login information which can only happen if you, the receiver of the malicious email, clicks the link and actually types in your email account login information.
If you were to click the link in the email, here is a screenshot of what the email harvesting website looks like:
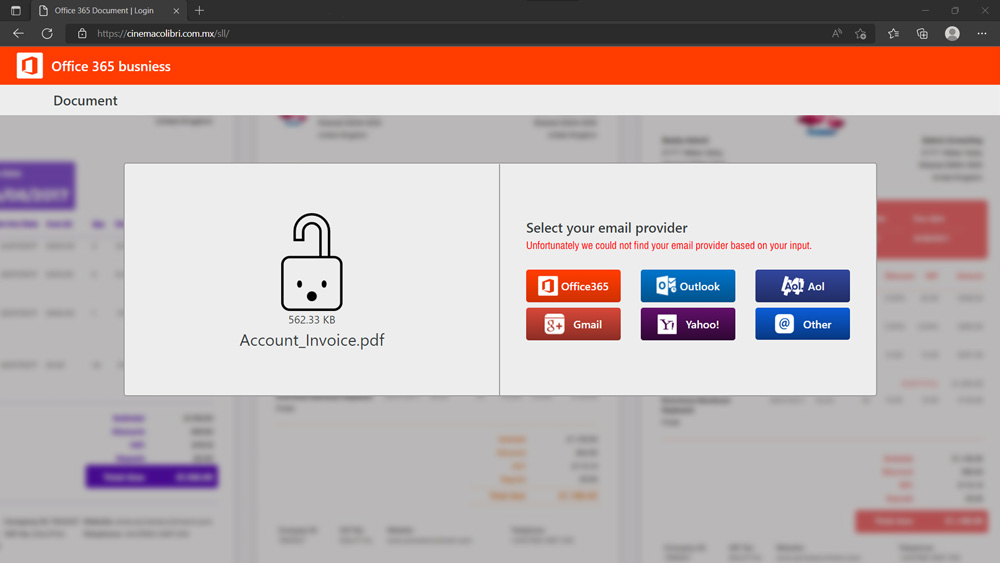
If you did click the link, but did NOT provide your email account login information to the malicious website, we believe there is no further cause for concern.
I used a test computer to click the link in the malicious email and submitted a fake email account login through it. After submitting, the website just redirects to Google with no further indication of anything happening. I rebooted the computer and did a full virus and malware scan and found nothing. It looks like this whole process was just trying to harvest email account logins.
If you DID submit your email account login information to the malicious website, you need to IMMEDIATELY log in to that email account and change your password. If you don't, it is likely that this nefarious character will change your account password themselves, thereby locking you out of your email account.
In working with our programming team yesterday and today, we did not find any indication that Workamper.com or our member database was compromised. We took down our website for about an hour yesterday evening while we investigated and hardened its security.
The email service account has been secured with new login authentication and more strict connection features. Our website and services are operating normally again now.
For those of you who immediately contacted us, thank you. Because of your prompt emails and phone calls, we were made aware of the problem within minutes of the event, and we were immediately able to initiate an investigation and deploy mitigation measures.
While our investigation is ongoing, we have achieved a state of containment, implemented additional enhanced security measures, and see no further evidence of unauthorized activity.
Based on what we have learned and implemented, we are evaluating further mitigation techniques to strengthen our website and third-party services against these kinds of attacks.
I thank you for your patience as we work expeditiously to complete our investigation and regret any concerns or inconvenience this may have caused you. We will continue to update our customers with the transparency they deserve.
Sincerely,
Luke Duquette
Technical Director
Workamper News
FAQs
1. Has my credit card data been compromised?
No. This incident did not compromise your credit card data. We never store your credit card information in our third-party email service. We utilize an industry standard method of securing your credit card data with our credit card processor that resides completely outside our website, Workamper.com. This ensures that neither Workamper News staff, administrators, website programmers, or anyone else has access to your credit card information. Your credit card info is safe.
2. Has my contact data been compromised?
Maybe. Our investigation has shown that the unauthorized user was able to log in to our third-party email service. In doing so, they would have been able to view contact data such as your name, your email, your phone number and your mailing address. We have no way to confirm that they looked at any of that customer data, but we can confirm they would not have been able to export the data out of the email service as that is not allowed. While it is possible that the unauthorized user could have attempted to copy and paste contact information, they would have been forced to do so one contact record at a time. This is highly unlikely, but again, we can't say for sure. To reiterate, the only personal information stored in the email provider would be your name and contact information. They did not have access to your credit card, resume, order history, etc on Workamper.com.
3. Has my account on Workamper.com been compromised?
No. Our investigation has shown no evidence of any unauthorized access to customer data in our website, Workamper.com.
4. What should I do to protect myself and my data?
If you clicked the link in the email, but did NOT submit your email login information to the spammer's website, we believe there is no need for further concern. If you DID submit your email login information, you need to immediately go change your password on your email account. I would advise you to update all website accounts you have that use that email address to log in with, especially if you are using the same password.
5. How can I get more information?
You may call us at 800-446-5627 or email us at [email protected], but please be advised that we have received an abundance of support requests in the past 24 hours due to this inciden, so we may be a bit slower than normal to respond.

